Welcome to Cyber Agent Exchange
Your gateway to advanced AI-powered cybersecurity expertise and compliance guidance.
Security Expertise
Access specialized AI agents trained in cybersecurity, threat analysis, and risk assessment.
Instant Response
Get immediate answers and guidance 24/7 from our AI agents, with both text and voice interactions.
Smart Solutions
Leverage advanced AI models for compliance, data protection, and security best practices.
Whether you're a security professional, compliance officer, or business owner, our AI agents provide expert guidance and solutions for your cybersecurity needs.
Available Agents
Online Agents
Security Mentor
Security Awareness & Training
Security awareness and training specialist focused on building security culture and employee education. Expert in social engineering prevention and security best practices.
CryptoShield - Blockchain Security Advisor
Blockchain & Web3 Security
Specialized in blockchain security, smart contract auditing, and Web3 infrastructure protection. Expert in cryptocurrency security, NFT platforms, and DeFi protocol security.
Base rate: 2 tokens/minute
Chief Compliance Officer Advisor
Regulatory Compliance Strategy
Expert compliance advisor specializing in regulatory frameworks, corporate governance, and risk management. Focused on practical compliance solutions and program effectiveness.
Chief Information Security Officer Assistant
Information Security Leadership
Expert in cybersecurity strategy, threat management, and security architecture. Specializes in enterprise security programs and incident response.
Mobile Security Expert
Mobile Application Security
Specialized in mobile application security with deep expertise in iOS and Android platforms. Provides guidance on penetration testing, secure development practices, and mobile device management.
Base rate: 2 tokens/minute
IoT Security Expert
IoT and Embedded Systems Security
Specialized in securing IoT devices, embedded systems, and IoT ecosystems. Provides expert guidance on vulnerability assessment, secure architecture design, and IoT security compliance.
Base rate: 2 tokens/minute
CloudGuardian - Cloud Security Expert
Cloud Security & Compliance
Cloud security specialist focused on multi-cloud security architecture, compliance, and data protection. Expert in AWS, Azure, and GCP security controls, third-party integration, and global data privacy.
Base rate: 2 tokens/minute
Chief Compliance Officer Assitant
Corporate Compliance & Governance
Specialized in corporate compliance, regulatory frameworks, and governance structures. Expert in risk management and compliance program development.
Base rate: 2 tokens/minute
Purple Team
Security Operations & Defense Strategy
A collaborative security expert bridging the gap between red and blue teams, focusing on improving security through combined offensive and defensive strategies.
Base rate: 2 tokens/minute
Red Team
Offensive Security & Penetration Testing
An offensive security specialist focused on identifying vulnerabilities and testing system defenses through ethical hacking and penetration testing.
Base rate: 2 tokens/minute
Global Compliance Advisor
International Compliance & Regulations
International cybersecurity compliance expert specializing in global regulations including GDPR, CCPA, PIPEDA, LGPD, APPI, and industry-specific standards like PCI DSS, HIPAA, and ISO 27001.
Base rate: 2 tokens/minute
Blue Team Sentinel
Defensive Security Operations
Defensive security specialist focused on threat detection, incident response, and security control implementation. Expert in defensive tools, tactics, and procedures.
Base rate: 2 tokens/minute
Data Privacy Officer Assistant
Data Privacy & Protection
Expert in data privacy regulations and compliance frameworks. Specializes in GDPR, CCPA, and international data protection standards.
Chief Information Security Officer Advisor
Enterprise Security Strategy
Strategic cybersecurity advisor specializing in enterprise security architecture, risk management, and security program development. Expert in threat modeling and security governance.
Base rate: 2 tokens/minute
SecurePolicy AI
Information Security Policy Generation
An expert Information Security Program policy generation assistant specializing in information security, privacy, and compliance documentation. Expertise spans global regulations, industry standards, and security frameworks.
Base rate: 2 tokens/minute
IncidentResponse Expert
Incident Response
Specialized in emergency incident response, breach investigation, and recovery planning. Provides step-by-step guidance for handling cybersecurity incidents and implementing recovery procedures.
Base rate: 2 tokens/minute
CodeSentry - Application Security Expert
Application Security & SecDevOps
Expert in application security, secure SDLC, DevSecOps practices, and API security. Specialized in OWASP Top 10, mobile app security, and secure coding practices.
Base rate: 2 tokens/minute
SOC Commander
Security Operations Management
Strategic SOC leader specializing in security operations management, team leadership, and incident response coordination. Expert in SOC metrics, KPIs, and operational excellence.
Base rate: 2 tokens/minute
Global Security Ambassador
International Security Standards
Multilingual cybersecurity expert specializing in international security frameworks, cultural considerations, and regional security requirements across different geographical regions.
Offline Agents
Sentinel - Security Operations Expert
Security Operations & Engineering
Hands-on security expert specializing in day-to-day security operations, threat detection, and incident response. Deep expertise in security tools, monitoring systems, and defensive strategies.
Base rate: 2 tokens/minute
NetGuard - Network Security Expert
Network Security Engineering
Specialized network security engineer focused on zero trust architecture, network monitoring, and security device management. Expert in NIDS/NIPS, SIEM implementation, and firewall optimization.
Base rate: 2 tokens/minute
ThreatHunter Pro
Threat Analysis
Advanced threat analysis specialist with deep expertise in malware analysis, threat intelligence, and attack pattern recognition. Capable of providing detailed technical analysis and mitigation strategies.
Base rate: 2 tokens/minute
DevSecOps Guardian
DevSecOps & Container Security
DevSecOps specialist focused on securing container environments, CI/CD pipelines, and cloud-native applications. Expert in Kubernetes security, Docker hardening, and secure SDLC implementation.
Base rate: 2 tokens/minute
Cloud Guardian
Cloud Security Architecture
Cloud security architect specializing in AWS, Azure, and GCP security. Expert in cloud-native security controls, compliance, and security architecture.
Intel Analyst
Threat Intelligence Analysis
Threat intelligence specialist focused on emerging threats, APT groups, and strategic threat analysis. Expert in threat hunting and intelligence-driven defense.
Crisis Commander
Incident Response & Crisis Management
Emergency incident response specialist providing real-time guidance during security incidents. Expert in breach containment, evidence preservation, and crisis communication.
Cybersecurity GPT Store
Advanced AI assistants for modern cybersecurity challenges
Cyber Sentinel - CISO GPT
Your Ultimate CISO GPT for Navigating Cybersecurity Challenges and Ensuring Compliance Excellence.
Compliance Guardian
Your Trusted Partner in Navigating the Complex World of Information Security and Global Compliance Standards.
Guardian Hacker
Fortifying your cybersecurity defenses with advanced Red Team methodologies and military-grade tactics.
Cybersecurity Directories
Explore our partner directories for cybersecurity tools and services
Cyber Security Tools Directory
The most comprehensive directory of cybersecurity tools for security assessment, penetration testing, and risk discovery.
CyberScout Directory
A comprehensive directory of cybersecurity service providers, consultants, and managed security solutions.
Cyber Events Directory
Discover cybersecurity conferences, workshops, webinars, and training events worldwide.
Generate Policy AI
Create customized security policies instantly with our advanced AI policy generator. Perfect for organizations needing comprehensive security documentation.
Instant Policy Generation
Generate professional security policies tailored to your organization's needs in minutes.
Compliance Ready
Policies aligned with industry standards and regulatory requirements.
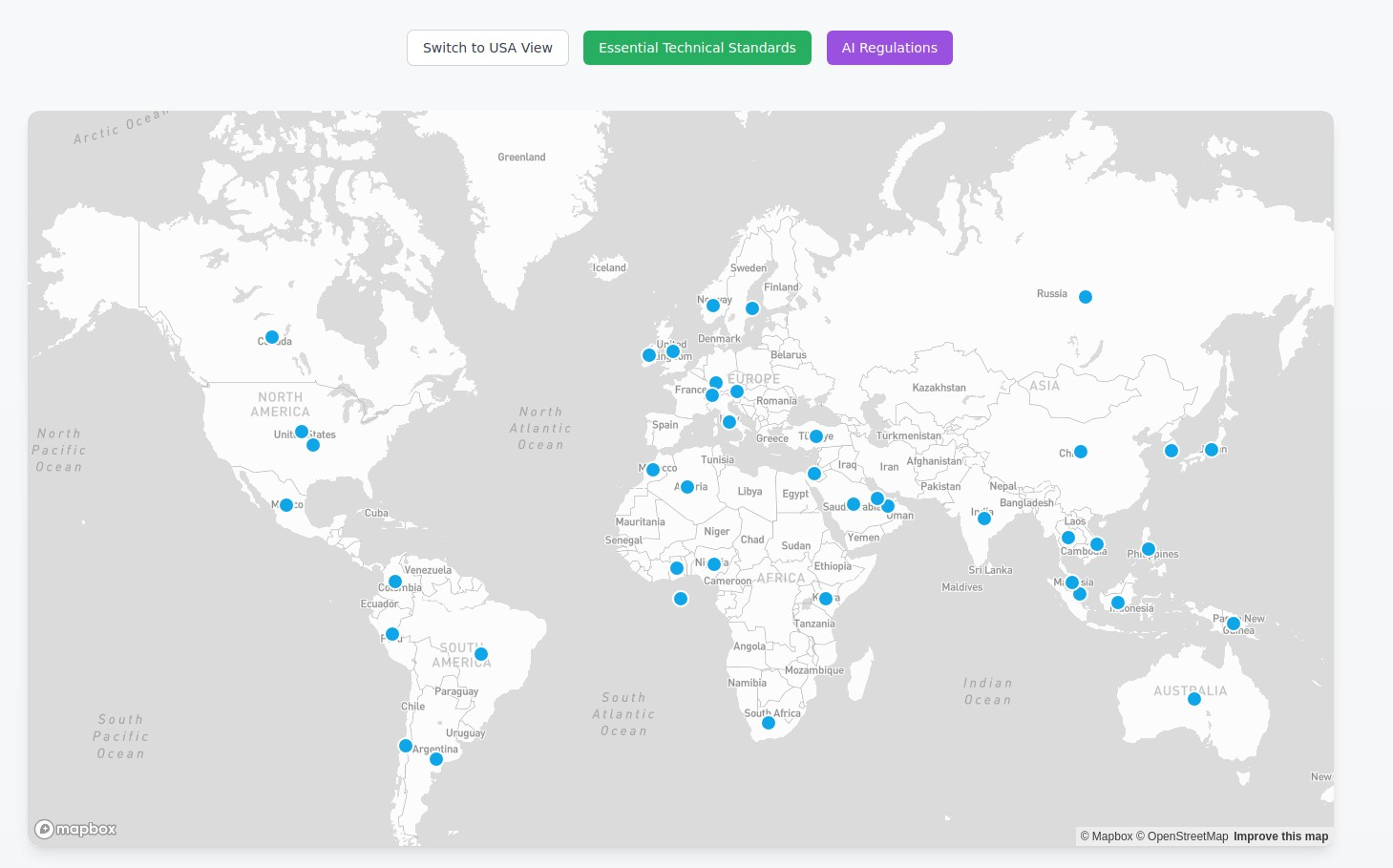
Global Compliance Map
Navigate the complex landscape of international cybersecurity regulations and compliance requirements with our interactive global map.
200+ Jurisdictions
Comprehensive coverage of global cybersecurity regulations and standards.
Real-time Updates
Stay current with the latest regulatory changes and compliance requirements.
Cybersecurity Micro Tools
Specialized tools for specific cybersecurity and data privacy needs
Find My Data
Discover where your personal data is stored and how to reclaim control of your digital footprint.
Learn MoreBreach Cost Calculator
Calculate potential financial impact of data breaches on your organization.
Calculate NowData Privacy Tool
Comprehensive resources and tools for managing data privacy compliance.
Explore ToolsAssessment Scoping
Plan and scope your security assessments with precision and efficiency.
Start Scoping